Authentication is a critical component of any security strategy. Today, we are going to discuss SQL Server authentication and how it is essential to securing your SQL Server environment, and the role Windows authentication plays.
Establishing a connection
It all starts with a connection. In order to establish a successful database connection, the client or application requires the following information:
- SQL Server fully-qualified domain name
- Instance name
- Port number
- Credentials (username and password) for authentication
For example, suppose you use online banking. In order to access your account, you are required to enter credentials for authentication purposes. The bank identifies you when you provide valid credentials and allows access to its services upon verification.
Similarly, when logging into SQL Server, users need to specify valid credentials so that SQL Server can authenticate their identity and grant the appropriate access.
SQL Server provides two modes of server authentication:
- Windows authentication
- SQL Server and Windows authentication mode (mixed-mode)
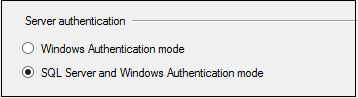
You can define these authentication methods during the installation of SQL Server, or change them later via a restart. It’s critical for database administrators to understand the differences between these authentication methods and implement them per their organization’s specific requirements.
Let’s dive in further to understand the advantages and disadvantages of both SQL Server and Windows authentication.
An overview of SQL Server authentication
Database administrators create SQL logins and provide appropriate permissions for users to authenticate themselves to SQL Server. Users need to specify the login and password while connecting to SQL Server as shown below.
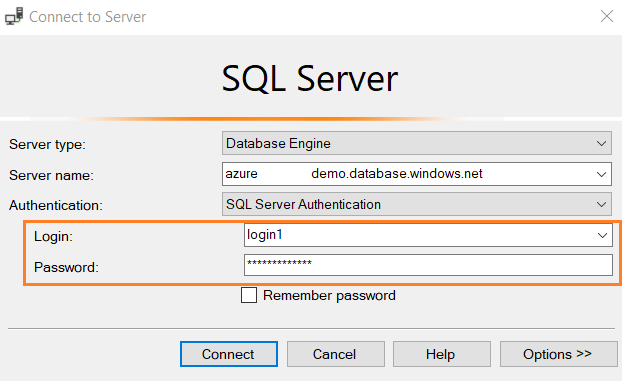
The user’s credentials are validated through the information stored in the master database. You can enforce the following policies for SQL Server logins.
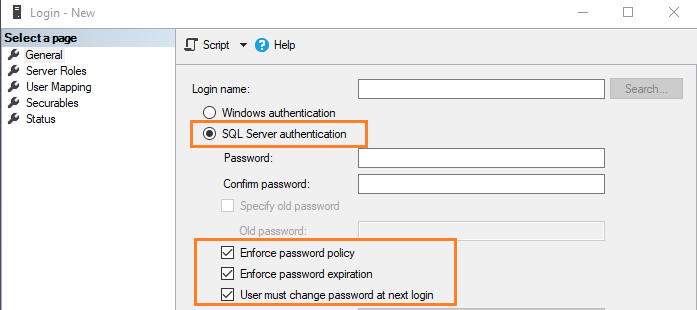
- Enforce password policy: The administrators can check this option to implement the Windows password policy for SQL Server logins. It includes specifying password length and complexity.
- Enforce password expiration: You can enforce the maximum age of a password. The password will be expired and needs to change as defined by the age criteria.
- User must change password at next login: The administrator assigns a password during SQL login creation. Once the user logs in with their credentials, they need to specify a new password, and the administrators will not be aware of this new password.
Note: All these configurations are at the individual SQL login level. Therefore, if you need to create multiple SQL logins, you must configure each account with the required policy.
We cannot enable only SQL authentication. To enable it, use the mixed authentication option which includes both Windows and SQL authentication.
Disadvantages of SQL Server authentication
There are quite a few limitations and disadvantages of using SQL Server authentication alone.
- Users need to remember the SQL login credentials and provide them in the connection string each time they connect to SQL Server. If you have multiple SQL Servers, it might be difficult for the user to keep track of the passwords for each instance.
- SQL Server stores the password in the master database in encrypted (hash) form. Hackers can steal the information by accessing the database. Since these encrypted credentials need to be passed over the network, this can increase the chances of user credentials being stolen.
- You cannot implement additional (customized) account policies with the SQL Server authentication logins.
- It increases the task of login management for database administrators. Database administrators do not have a central management console for managing logins across all instances.
Suppose you have 500+ SQL instances and a user requires access to all these instances. In this case, it would be a tedious task for the database administrator to connect to each instance and create user logins. Similarly, if a person left the organization, the database administrator needs to find out that individual’s SQL logins and remove them from all these instances. This can be a very time-consuming process.
- You might get orphan user issues when moving a database to different instances, and it might happen due to a SID mismatch in the master and user database on the new instance.
- You need to manage the security policies for each SQL login. You cannot define a universal policy for all accounts in your organization. For a large database footprint, it is an arduous task to define the policy for each individual login.
Best use cases for SQL Server authentication
- It can help older applications and third-party software connect databases if they do not support Windows (AD) authentication.
- You might require users from untrusted domains to connect to SQL Server. In this case, the application can specify SQL logins in the connection strings and connect to the database.
- To connect standalone SQL instances that are not part of Active Directory (AD) groups.
- It can help SQL Server to support web applications where users create their own identities.
- The administrators share a common ID for connecting to SQL Server using Active Directory authentication in a few cases. This connection pooling is not a good practice. In this case, you can create separate logins for each user and connect to the database using their credentials.
- By default, if you implement SQL Database in the cloud, i.e., Azure SQL Database or AWS RDS, you are provided login credentials for SQL Server authentication. Later, if required, you can configure AD-based authentication.
- You can use it to connect from cross-operating systems such as Linux and macOS.
An overview of Windows authentication
In Windows authentication, the user should first authenticate himself within Active Directory. SQL Server authenticates users through the Windows principal token in the OS. With that, SQL Server does not ask for a password for identity validation. Therefore, Windows confirms users’ identities for authentication. SQL Server does not store the credentials in the Windows authentication. The connection using Windows authentication is called a trusted or integrated connection.
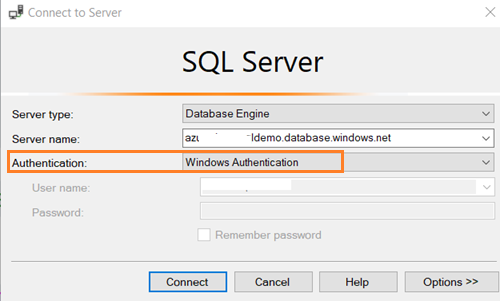
Note: Windows authentication is the default authentication method when you install SQL Server.
Advantages of Windows authentication
- Windows authentication is a secure way of connecting to SQL Server, and it uses the tokens and SPNs for authentication purposes using the Kerberos authentication protocol. Therefore, it does not send passwords across the network, and it safeguards stealing passwords across the network.
- SQL Server does not store the user’s credentials.
- It uses Kerberos security protocol, and you can implement password policies such as complex passwords, account lockouts and password expiration. This password policy can be implemented at the organization level across all servers. Therefore, you can control user security policies at the organization level instead of at the individual login level like with SQL Server authentication.
- Windows authentication enables the separation of duties. The Active Directory (AD) team manages the AD users. Whereas, the DBA adds AD users in the SQL instances and provides appropriate permissions.
- Active Directory helps to create Windows groups. The AD team can add multiple people that require equal access in an AD group. Later, you can add the group in the SQL instance and provide permissions at the group level. Therefore, if a new person joins, once he is part of the AD group, database access is automatically granted across the server where this AD group exists. Similarly, once a user moves from the organization and their ID is removed from these AD groups, they can no longer access the database.
Disadvantages of Windows authentication
- If you only use Windows authentication for SQL Server, all users should be part of the Active Directory.
- DBAs do not have control over the AD logins and groups.
- The AD group membership is not known to the DBA. You do not get a notification if a user is added or removed from the AD groups.
Summary
This blog post outlines the key components of SQL Server authentication and Windows authentication. I hope it helps you understand the differences between these authentication methods to decide which works best for your business and circumstances.
SQL Server authentication can be used on the same machine as SQL Server or on a remote connection. If you work in an Active Directory environment, Windows authentication is recommended to use. If you work in a non-Active Directory environment, you can utilize SQL Server authentication for database connections.
Windows authentication does provide more security and flexibility for managing logins in SQL Server. Therefore, you should use it whenever feasible.